FIPS 140-3
Validate your product against the newly released version of the FIPS standard.

FIPS 140-3
Validate your product against the newly released version of the FIPS standard.
FIPS 140-3 Is Finally Here
The Federal Information Processing Standard 140-3 (FIPS 140-3) is a U.S. and Canadian co-sponsored security standard for hardware, software, and firmware solutions. In U.S. government procurement, all solutions that use cryptography must complete FIPS 140-3 validation to ensure end users receive a high degree of security, assurance, and dependability.
Is your certification strategy aligned with the recently released timelines and new standard Discuss your FIPS 140-3 validation approach and ensure your project is successfully conducted against changes in requirements, timelines, and processes.
Download Corsec’s FIPS 140-3 Overview, covering the standard, requirements, and level.
The Standard: FIPS 140-3
 The use of FIPS 140-3 validated products is mandated by Section 5131 of the Information Technology Management Reform Act of 1996.
The use of FIPS 140-3 validated products is mandated by Section 5131 of the Information Technology Management Reform Act of 1996.
 All products sold into U.S. federal agencies are required to complete FIPS 140-3 validation if they use cryptography in security systems that process Sensitive But Unclassified (SBU) information.
All products sold into U.S. federal agencies are required to complete FIPS 140-3 validation if they use cryptography in security systems that process Sensitive But Unclassified (SBU) information.
 Security requirements are outlined in full within the NIST FIPS 140-3 PUB.
Security requirements are outlined in full within the NIST FIPS 140-3 PUB.
FIPS Inside & FIPS Compliance
Corsec details the differences between FIPS 140-3 Validation, FIPS Compliant, and FIPS Inside.
Your customer requests, timelines, and product will all have an influence on which approach is best suited for your company. Review the white-paper to learn more.
The Requirements: FIPS 140-3
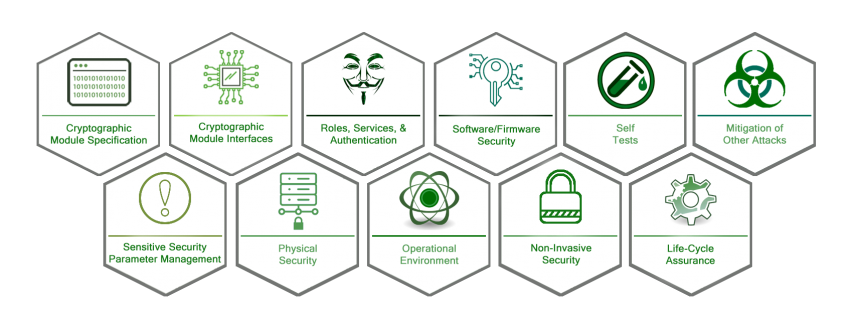
FIPS 140-3 contains eleven Derived Test Requirements (DTRs) that detail the requirements that must be provided to demonstrate conformance to the standard. Each section also describes the methods that the testing lab will take to test the module.
The eleven sections of FIPS 140-3 have been updated from the previous FIPS 140-2 version of the standard.
Cryptographic Module Specification:
The new standard defines five types of cryptographic modules or boundaries that can achieve validations; hardware module, firmware module, software module, hybrid-software module, and hybrid-firmware module. Hybrid modules, which were originally restricted to Level 1 validations in FIPS 140-2, no longer have a Level limitation.
Cryptographic Module Interfaces:
This section defines the interfaces or commands used by each module type, the new interfaces include; Hardware Module Interfaces (HMI), Software or Firmware Module Interfaces (SFMI), Hybrid-Software Module Interfaces (HSMI), Hybrid-Firmware Module Interfaces (HFMI), and Control Output Interface.
Software/Firmware Security:
This new section introduces Integrity Testing. This section does not apply to Hardware specific embodiments.
Roles, Services, & Authentication:
Roles: 1.) Crypto Officer Role, 2.) User Role, and 3.) Maintenance Role
The new FIPS 140-3 standard only mandates the Crypto Officer Role.
Services: 1.) Show Status, 2.) Perform Self-Tests, 3.) Perform Approved Security Function, 4.) Show Modules Versioning Information, and 4.) Perform Zeroization
Authentication: Level 4 now requires multi factor identity-based authentication.
Operational Environment:
Updates to this section include the elimination of the need for software modules at a Level 2 to be Common Criteria (CC) certified. However, there are many new requirements that coincide with CC that need to be addressed.
Physical Security:
Embodiments: 1.) Single-chip, 2.) Multiple-chip, and 3.) Multiple-chip Standalone
There are additional requirements at Level 2 (definition changes), Level 3 (tamper evidence seals), and Level 4 (EFP).
Non-Invasive Security:
This section outlines documentation and testing requirements for protecting the module from attacks performed in the absence of direct physical contact to components.
Sensitive Security Parameter Management (SSPs):
A new section in FIPS 140-3. SSPs include both Critical Security Parameters (CSPs) and Public Security Parameters (PSPs). This section covers SSP entry and output requirements at each level; as well as information on Random Bit Generation (RBG), CSP encryption, and Zeroisation.
Self-Tests:
New requirements for Periodic Self-Tests and Conditional Fault-Detection Tests have been added in addition to renaming Power On Self Tests to Pre-Operational Self-Tests.
Life-Cycle Assurance:
This section is dedicated to security requirements on how the module was designed, developed, and operates.
This section also includes requirements for the module’s End of Life. Additionally, the requirements from FIPS 140-2’s section on Finite State Model (FSM) have been absorbed into this section.
Mitigation of Other Attacks:
A section to address any additional attack mitigating functionality that was not directly called out in previous test requirements.
FIPS Inside & FIPS Compliance
Corsec details the differences between FIPS 140-2 Validation, FIPS Compliant, and FIPS Inside.
Your customer requests, timelines, and product will all have an influence on which approach is best suited for your company. Review the white-paper to learn more.
The Levels: FIPS 140-3
Within each of the eleven DTRs, there are four increasing qualitative security levels. At each level, greater amounts of evidence and engineering are required of the product in order to show compliance with the standard. FIPS 140-3 is retaining the 4 levels of validation:
 Level 1
Level 1
Previous Requirements
 Validation of at least one approved algorithm or security function
Validation of at least one approved algorithm or security function
 Production-grade evaluated components
Production-grade evaluated components
 Level 2
Level 2
Previous Requirements
 All Level 1 requirements
All Level 1 requirements
 Role-based authentication & physical security requirements for tamper evidence
Role-based authentication & physical security requirements for tamper evidence
 Level 3
Level 3
Previous Requirements
 All Level 1 and 2 requirements
All Level 1 and 2 requirements
 Identity-based authentication & physical security mechanisms for tamper detection & tamper response
Identity-based authentication & physical security mechanisms for tamper detection & tamper response
 Level 4
Level 4
Previous Requirements
 All Level 1, 2, and 3 requirements
All Level 1, 2, and 3 requirements
 Physical security mechanisms to detect and reply to tampering; including environmental attacks
Physical security mechanisms to detect and reply to tampering; including environmental attacks
The Process: Done Once, Done Right
Corsec’s Three-Step Methodology helps to decrease risk, increase security, and accelerate sales; guaranteeing validation success – Done Once, Done Right!

Determining the appropriate approach for your FIPS 140-3 validation is essential; depending on your product, the level you pursue, the boundary you draw, and the engineering changes required, your path to certification could alter greatly.
Corsec participates in numerous committees, technical working groups, certification leadership positions, and industry events. As more information develops, we will deliver updates. Stay informed on all the program details, requirements, and timelines associated with FIPS 140-3.
